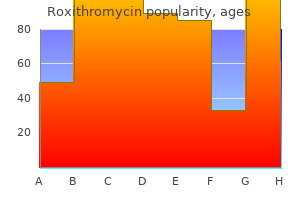
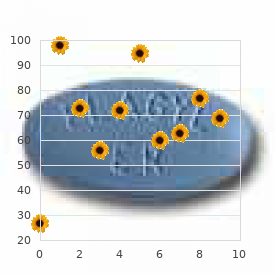
"Purchase roxithromycin in united states online, antibiotics for sinus infection wiki".
By: P. Kaelin, MD
Program Director, Drexel University College of Medicine
Among heroin users antibiotic herpes 150 mg roxithromycin mastercard, Hispanics were only 75 percent as likely as whites to complete a treatment episode (Mennis and Stahler antibiotics for sinus infection allergic to penicillin buy cheap roxithromycin 150 mg online, 2016) disturbed the infection buy roxithromycin line. This study found that nonwhite race and low income newest antibiotics for acne buy 150 mg roxithromycin overnight delivery, as well as previous incarceration and having experienced drug-related discrimination by medical providers, were associated with significantly lower rates of treatment enrollment (Liebling et al. Individuals involved in the criminal justice system also face barriers to effective treatment. While these individuals have high rates of substance use disorder (6080 percent), their treatment utilization is low. However, a minority (34 percent) of arrestees with drug use histories had received substance use disorder treatment during their lifetime, and only 14 percent had obtained such treatment during the year prior to their arrest. Receipt of mental health treatment services also is extremely low in this population despite a high prevalence of mental health problems. When treatment with medication is offered, it is typically limited to detoxification, and often is provided only to pregnant women. Moreover, about half of drug courts have a specific policy against use of treatment with medication. Lack of treatment uptake in the criminal justice system may reflect state and local regulations, security concerns, institutional philosophy, and availability and resources. Additional research is needed on strategies for how best to integrate treatment into the criminal justice system at all stages (Belenko et al. To enhance these benefits, additional research could examine several relevant areas, such as (1) development of new medications; (2) testing of the efficacy of combination drugs. The enormity of the current opioid crisis necessitates an immediate and massive expansion of treatment capacity to provide evidence-based treatment and recovery to millions of individuals. The committee recommends that schools for health professional education, professional societies, and state licensing boards require and provide basic training in the treatment of opioid use disorder for health care providers, including but not limited to physicians, nurses, pharmacists, dentists, physician assistants, psychologists, and social workers (Recommendation 5-7). Department of Health and Human Services and state health financing agencies remove impediments to full coverage of medications approved by the U. Food and Drug Administration for treatment of opioid use disorder (Recommendation 5-8). Many of the tools of drug policy are aimed at reducing or ending the use of drugs. These tools utilize a variety of methods, including individual rehabilitation and treatment, enforcement of criminal sanctions against drug use or distribution, and public communication campaigns aimed at preventing drug use. The priority of the harm reduction approach, in contrast, is minimizing the negative consequences of drug use instead of focusing solely on reducing drug use itself. Two of the most significant harms of opioid use are overdose and transmission of bloodborne infections due to injection drug use. As discussed in Chapter 4, opioid-related overdoses have soared in recent years; in 2015, more than 33,000 people died from opioid overdoses, nearly half of which involved a prescription opioid (Rudd et al. Strategies for reducing the harms of opioid use may include dispensing naloxone for use in reversing overdose, providing services that facilitate safer drug use (syringe exchange, supervised injection facilities, and drug checking), and implementing behavioral interventions. Changes in drug laws also can be effective (see Box 5-4 for an international example). Often, harm reduction strategies are implemented together (see Box 5-5 for an example). Thus, naloxone is provided along with training in how to use it, and syringe exchange facilities also facilitate treatment admission or other services, educate users about overdose prevention and abscess and wound care, and provide training in the use of naloxone. As a result, people who use drugs are considered "physically ill or sick," not "criminal" (Laqueur, 2014). Treatment of the substance use disorder was aggressively emphasized (Bushak et al. Possession of a small amount (up to a 10-day supply) of drugs is now dealt with by the local Commission for the Dissuasion of Drug Addiction, composed of an attorney, physician, and social worker. Approximately 90 percent of antidrug resources in Portugal is now spent on prevention and treatment, with the rest going to incarceration and other punishment. The increased health care costs are thought to be offset by cost reductions in the penal system.
The network fades away and a dozen or a hundred individual workstations look to the user like one big happy time-sharing machine are antibiotics for uti expensive discount roxithromycin 150mg online. Remote disks are automatically mounted as necessary infection 6 months after hysterectomy buy roxithromycin online, and files are accessed transparently tetracycline antibiotics for acne treatment discount roxithromycin 150 mg otc. Alternatively antibiotics for acne and side effects 150mg roxithromycin fast delivery, workstations can be set to mount the disks on the server automatically at boot time. The server sends you back a list of the files that are in the remote directory, as well as a magic cookie for each of the files that the remote directory contains. Once a magic cookie is issued for a file, that file handle will remain good even if the server is shut down and rebooted, as long as the file continues to exist and no major changes are made to the configuration of the server. Sun would have us believe that the advantage of a connectionless, stateless system is that clients can continue using a network file server even if that server crashes and restarts because there is no connection that must be reestablished, and all of the state information associated with the remote mount is kept on the client. As a result, an elaborate restart procedure after the crash is necessary to recover state. Instead of hiding this complexity in the lockd program, where it is rarely tested and can only benefit locks, it could have been put into the main protocol, thoroughly debugged, and made available to all programs. Deciding which method is the grosser of the two No File Security 287 is an exercise left to the reader. And you better not go on vacation with the mail(1) program still running if you want your mail file to be around when you return. You better be sure that your network file system has some built-in security to prevent these sorts of attacks. Instead you have to return to him several times so that he can demand-page in the necessary information driven by the faults you are forced to take. Knowledgeable people informed me that I had to visit a Grand Exalted Wizard who would add my name and password to the "Kerberos" database. The Grand Exalted Wizard told me I was all set: from now on whenever I logged in I would automatically be granted the appropriate network privileges. Now it is time to pack up and go home, so I try to write my files back out over the network. I poke around a bit and find that the problem is that when your Kerberos privileges expire, nfsauth crashes. Well, it turns out that I almost always work for longer than eight hours, so this becomes a bit of a routine. Well, I ask, how about at least fixing nfsauth so that instead of crashing, it just hangs around and waits for your new Kerberos privileges to arrive? To get the magic cookie for the root directory of a file system, you need to mount the file system. A special file on the server called /etc/exports lists the exported file systems and the computers to which the file systems are allowed to be exported. Any requests for superuser on the network are automatically mapped to the "nobody" user, which has no privileges. If you are logged in as superuser, there is no easy way for you to regain your privilege-no program you can run, no password you can type. This is a deep and important theological question that has puzzled humankind for millennia. Thus when the manifestation of the divine spirit, binmail, attempts to create a mailbox on a remote server on a monotheistic Unix, it will be able to invoke the divine change-owner command so as to make it profane enough for you to touch it without spontaneously combusting and having your eternal soul damned to hell. It can be made to work, but only with a great deal of difficulty and a very user-visible performance penalty. We have taken the recommended steps to correct this problem, but until Sun gets us a fix, it will reoccur occasionally. The symptoms of this problem are: When you go to log in or to access a file, it looks as though the file is garbage or is a completely different file. You can do this by logging directly into the server that your files are on and looking at the files. If you discover that your files are trashed locally, but not on the server, all you have to do is to log out locally and try again.
Science Coursetaking by High School Completers All ninth graders who began high school in 2009 and completed in 2013 took at least one science course antibiotics for acne is it safe discount roxithromycin amex, with 79% taking at least one general science course (but no advanced science) and 21% taking at least one advanced course (Table 1-16) bacteria hpf in urinalysis generic roxithromycin 150 mg on line. Virtually all students (98%) took biology antibiotic before dental work order generic roxithromycin pills, 76% took chemistry antibiotic nerve damage cheap roxithromycin 150mg online, and fewer (41%) took physics. Among all racial or ethnic groups, Asian students were the most likely to take advanced science courses, by a large margin. For example, 25% of Asian students took advanced chemistry, compared with 9% of white students, 3% of black students, and 5% of Hispanic students. The percentage of students who took general physics was not significantly different among white, black, and Hispanic students. For example, 78% of female students took chemistry, compared with 73% of male students. The pattern reversed slightly for physics, with 40% of female students taking physics, compared with 43% of male students. In advanced coursetaking, female students were slightly more likely than male students to take advanced biology (13% versus 10%) and slightly less likely to take advanced physics (4% versus 7%). White female students were more likely than white male students to take chemistry (79% versus 73%), and white male students were more likely than white female students to take physics (45% versus 39%). Black female students were more likely to take at least one advanced science course than their male counterparts (18% versus 9%), specifically advanced biology (12% versus 5%). For example, students who enrolled in a course above algebra 1 in ninth grade took advanced biology, chemistry, and physics at higher rates, compared with students who enrolled in algebra 1 in ninth grade (19% versus 7% for biology, 14% versus 4% for chemistry, and 11% versus 2% for physics). About 85% of students at public and private schools took general biology, but students at private schools took general chemistry and physics at higher rates than their public school counterparts (81% versus 67% and 54% versus 35%, respectively). Asian, black or African American, white, and other races refer to individuals who are not of Hispanic origin. The Bureau of Labor Statistics projects 23% growth from 2014 to 2024 in the computer systems design and related services industry-from 1,777,700 jobs in 2014 to 2,186,600 jobs in 2024 (U. In light of this projected growth, educators and policymakers, concerned that too few students are exposed to computer science instruction in school, are working to broaden access to computer science courses (Change the Equation 2016; Nager and Atkinson 2016). Several efforts related to computer science education are currently under way and these developments, detailed in the sidebar Focus on Computer Science, herald a new focus on computer science in K12 education. An earlier federal initiative, Computer Science for All, was announced by the Obama administration in early 2016. Although Congress did not approve the specific funding called for in the Computer Science for All initiative, other efforts related to it, such as investments by the National Science Foundation and the Corporation for National and Community Service to support and train computer science teachers, are moving forward. The Every Student Succeeds Act specifically includes computer science as part of science, technology, engineering, and mathematics education subjects and includes computer science with other core subjects, such as English, reading, science, and mathematics, in its definition of a "well-rounded education. The course, designed to increase the number and diversity of high school students taking computer science, focuses on several topics in addition to programming, including working with data, computational thinking processes, algorithms, understanding the Internet, and cybersecurity. The K12 Computer Science Framework outlines the essential computer science concepts and practices that students should know by the end of grades 2, 5, 8, and 12. About two and a half times as many male students (21%) earned engineering and technology credits compared with female students (8%). No significant difference was detected in the percentage of male and female students earning credits for computer and information sciences. It is important to note that computer and information sciences credits reported above included credits earned for introductory courses as well as applied courses focused on learning and using specific software programs. These introductory courses do not fall under the more rigorous definition of computer science as "the study of computers and algorithmic processes, including their principles, design, implementation and impact on society" endorsed by the new K12 Computer Science Framework (K-12 Computer Science Framework 2016). Science and Engineering Indicators 2018 Data collected as part of a multiyear research effort by Gallup and Google give further insight into the state of computer science education in the United States (Google Inc. Gallup interviewed nationally representative samples of students, parents, teachers, principals, and superintendents in late 2015 and early 2016. Data from the survey of principals reveal the extent of student access to computer science courses.
Buy generic roxithromycin. Acoustic perforated wood walls panels.